Introduction
Reason for these Cyber Security Directions
In an increasingly digital world, the threats posed by cyberattacks have become a significant concern for organizations worldwide. Recognizing the urgency of the situation, on April 28, 2022, the Indian Computer Emergency Response Team (“CERT-IN”) introduced new directives that mandate all cybersecurity incidents be reported within a stringent timeframe. This move marks a significant shift in India’s approach to cybersecurity, underscoring the need for rapid response and heightened vigilance.
Scenario before these Directions
Prior to these directives, many organizations struggled with limited visibility into cybersecurity threats, leading to incidents that were either inadequately reported or overlooked altogether. The lack of comprehensive analysis and investigation of these incidents often left critical gaps in understanding and mitigating cyber risks. With the implementation of this directive, organizations are now compelled to reassess their internal cybersecurity protocols, ensuring that robust measures are in place to meet these new reporting requirements.
Highlights of the CERT-IN Directions
Applicability
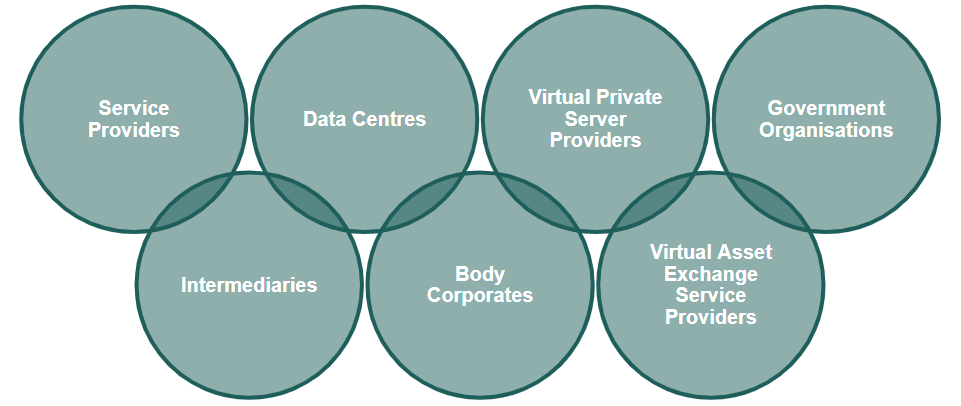
These directions cover all organisations that come within the purview of the Information Technology Act, 2000.
Individuals, Enterprises, and VPN Service Providers are excluded from following these directions.
Types of Incidents to be Reported
The directions provide an exhaustive list of incidents that need to be reported within the timeframe mentioned (refer Annexure I). In addition to these directions, the entities to whom these directions are applicable also need to continue following Rule 12 of the Information Technology (The Indian Computer Emergency Response Team and Manner of Performing Functions and Duties) Rules, 2013, and report the incidents as elaborated therein.
Timelines and How to Report
Timeline. All incidents need to be reported to CERT-IN within 6 (Six) hours from the occurrence of the incident or of the incident being brought to the respective Point of Contact’s (“POC”) notice.
Reporting. Incidents can be reported to CERT-IN via Email at ‘incidents@cert-in.org.in’, over Phone at ‘1800-11-4949’ or via Fax at ‘1800-11-6969’. Further details regarding reporting and the format to be followed are uploaded at ‘www.cert-in.org.in’.
Designated Point of Contact (POC)
The reporting entities are mandated to designate a POC to interface with CERT-IN. All communications from CERT-IN seeking information and providing directions for compliance shall be sent to the said POC.
Maintenance of Logs
The directions mandate the reporting entities to enable logs of all their information and communications technology systems (“ICT”) and maintain them securely for a period of 180 days. The ambit of this direction is broad and has potential of bringing in such entities who do not have physical presence in India but deal with any computer source present in India.
ICT Clock Synchronization
Organizations are required to synchronize the clocks of all their ICT systems by connecting to the Network Time Protocol (“NTP”) Server provided by the National Informatics Centre (“NIC”) or the National Physical Laboratory (“NPL”), or by using NTP servers that can be traced back to these sources.
The details of the NTP Servers of NIC and NPL are currently as follows:
NIC – ‘samay1.nic.in’, ‘samay2.nic.in’
NPL – ‘time.nplindia.org’
However, the government has provided some relief, that not all companies are required to synchronize their system clocks with the time provided by the NIC or the NPL. Organizations with infrastructure across multiple regions, such as cloud service providers, are permitted to use their own time sources, provided there is no significant deviation from the time set by NPL and NIC.
Challenges Faced and Recommendations
Challenges
- Limited Infrastructure and Resources: Many companies, especially tech startups may struggle to develop the necessary capabilities for large-scale data collection, storage, and management needed to report incidents within a six-hour timeframe.
- Stringent Guidelines compared to International Standards: For example, Singapore’s data protection laws require cyber breaches to be reported within three days, which aligns with the General Data Protection Regulation (GDPR).
- Increasing complexity of Cybercrime Detection: Identifying cybersecurity breaches can take days or even months. Additionally, the new guidelines have expanded the list of reportable incidents from 10 to 20, now including attacks on IoT devices. Currently, many organizations do not have an integrated framework that can monitor breaches across different platforms and devices, making it even more challenging to detect and report incidents.
Recommendations to comply with the 6 hours Timeframe
- Reassess Practices and Procedures: Organisations, especially tech startups should review and update their breach reporting protocols to align with CERT-IN directions. This includes evaluating breach severity, clarifying reporting responsibilities among involved parties, and planning for non-compliance risks.
- Enhance Organizational Capabilities: Startups need to strengthen their ability to quickly identify and report cyber breaches. This includes training staff, conducting regular security audits, and managing personal device use. Given their limited resources, robust cybersecurity practices are vital for startups to protect against attacks and ensure their growth.
- Enable and Maintain Logs: CERT-IN requires organizations to enable and maintain logs. Startups should carefully select which logs to maintain based on their industry to ensure they can promptly identify and report cyber incidents, staying compliant with the reporting timeframe.
Consequences for Non-compliance
- Failure to comply with the directions can result in imprisonment for up to 1 year and/ or a fine of up to INR 1 Crore (approximately USD 1,20,000).
- Other penalties under the IT Act may also apply, such as the confiscation of the involved computer or computer system.
- If a company commits the offence, anyone responsible for the company’s operations at the time will also be liable. Furthermore, if the contravention occurred with the consent, involvement, or neglect of a director, manager, secretary, or other officer, that individual will also be considered guilty and subject to legal action.
Conclusion
The CERT-IN Directions issued on 28th April 2022 mark a significant step towards strengthening India’s cybersecurity framework. These directions introduce stringent reporting timelines, enhanced data retention requirements, and new compliance obligations for service providers, intermediaries, and other key entities. By mandating swift reporting of cyber incidents within 6 hours and enforcing strict penalties for non-compliance, CERT-IN aims to bolster the security and trustworthiness of India’s digital infrastructure. The intention behind the introduction of these measures is laudable but from a compliance point of view, the direction can be overreaching and may not be the most efficient manner of dealing with cybersecurity threats.
Annexure
Types of Incidents to be reported include:
- Attacks or malicious/suspicious activities affecting systems/servers/software/applications related to Artificial Intelligence and Machine Learning.
- Targeted scanning/probing of critical networks/systems.
- Compromise of critical systems/information.
- Unauthorised access of IT systems/data.
- Defacement of website or intrusion into a website and unauthorised changes such as inserting malicious code, links to external websites etc.
- Malicious code attacks such as spreading of virus/worm/Trojan/Bots/Spyware/Ransomware/ Cryptominers.
- Attack on servers such as Database, Mail and DNS and network devices such as Routers.
- Identity Theft, spoofing and phishing attacks.
- Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks.
- Attacks on Critical infrastructure, SCADA and operational technology systems and Wireless networks.
- Attacks on Application such as E-Governance, E-Commerce etc.
- Data Breach.
- Data Leak.
- Attacks on Internet of Things (IoT) devices and associated systems, networks, software, servers.
- Attacks or incident affecting Digital Payment systems.
- Attacks through Malicious mobile Apps.
- Fake mobile Apps.
- Unauthorised access to social media accounts.
- Attacks or malicious/suspicious activities affecting Cloud computing systems/servers/software/applications.
- Attacks or malicious/suspicious activities affecting systems/servers/networks/software/applications related to Big Data, Blockchain, virtual assets, virtual asset exchanges, custodian wallets, Robotics, 3D and 4D Printing, additive manufacturing, Drones.

